Table of Contents
Tokenization means a process in which sensitive card and payment details of a customer are converted into random, unique, and meaningless strings of characters, known as tokens. These token values are generated randomly and flow securely into the transaction network without exposing any sensitive details. The payment details include the account number, PAN, CVV, expiration dates, and other relevant information. For example, conversion of a card number, ‘1574 5638 7985,’ into ‘gh5k 78uo albf.’
However, tokens are stored in a secure vault, known as a ‘token vault,’ which reduces the risk of data breach and theft. Therefore, even if anyone alters the security and gains access to these tokens, they won’t be able to perform a fraudulent transaction, as they don’t have access to the original payment details. Therefore, this is how tokenization protects customer data and privacy.
Tokenization is an essential component of a payment architecture for any business utilizing e-commerce.
With a clarity on what is tokenization, this blog will further break down the types, working, and benefits of tokenization.
Let’s get started!
Discover other key elements and build a secure and compliant payment architecture for your business. Download our E-guide
Types of Tokenization
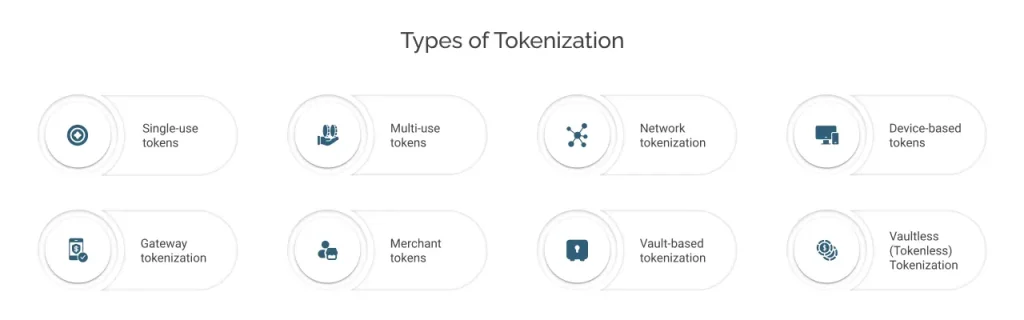
Learn about different types of tokenization solutions in payments:
1. Single-use tokens
Single-use tokens are generated and are valid only for a one-time transaction. Once the transaction is processed, whether successful or unsuccessful, the token becomes invalid and cannot be reused.
It prevents replay attacks, as the token cannot be reused for fraudulent purchases, and the customer data is not stored.
When to use?
Single-use tokens can be used:
- With high-value transactions
- For one-time purchases
- When there is no need to store payment data
2. Multi-use tokens
A multi-use token can be used for multiple transactions. These remain valid for a particular year and represent the same account across different purchases for a merchant.
These tokens are created when the customer checks the checkbox to store the payment details. These are mapped back to the same underlying card data in a secure vault. This makes it convenient for customers who want to make repeat purchases with the same merchant, eliminating the need to re-enter the payment details.
When to use?
Multi-use tokens can be used:
- For recurring transactions and subscriptions
- For repeated purchases by the same customer
- For a one-click checkout experience
3. Network tokenization
Network tokens are issued directly by card networks such as Visa, Mastercard, American Express, and other payment networks. These are issued and managed by the card network.
These tokens can be used across multiple merchants, platforms, and payment service providers without requiring separate tokens.
There is no need for manual intervention, as tokens update automatically with new payment information. It replaces card details at every stage of the transaction, providing end-to-end protection.
This type of tokenization is considered more secure because the issuing bank has direct control over it.
When to use?
- Suitable for digital wallet transactions such as Apple Pay, Google Pay, Samsung Pay, and more.
- For cross-merchant transactions
4. Device-based tokens
A subset of network tokenization that is used with digital wallets and mobile devices. The sensitive card data is tokenized and stored in a secure element or trusted execution environment (TEE) on a particular device.
These tokens are only valid for that specific device, and user authentication using fingerprint or Face ID is often required for transactions.
When to use?
- In mobile and contactless payment scenarios
- Across retail and e-commerce with mobile checkout
- For one-click payments on specific devices
5. Gateway tokenization
Gateway tokens are generated and managed by payment gateways or acquiring banks, rather than card networks. It is much simpler to implement for the merchants already integrated with a payment gateway.
When to use?
- For recurring and subscription-based billing models
6. Merchant tokens
Merchant tokens are generated for a merchant by their chosen tokenization provider. These are created when a cardholder uses their card to process a transaction.
These tokens are provider-specific. While also, they may not work across different payment processors.
When to use:
- When merchants work with a single payment processor
- With custom payment processing solutions
7. Vault-based tokenization
The sensitive payment data in vault-based tokenization is securely stored in an encrypted vault with tokens generated for each transaction. The secure vault is maintained by the payment processor or the bank. In this, the original card data is stored, and tokens are mapped to the vault data via a lookup table.
However, there is a point of vulnerability if the vault is breached.
When to use?
- Enterprises with a centralized payment infrastructure
- Organizations with existing vault infrastructure
8. Vaultless (Tokenless) Tokenization
In vaultless tokenization, the vault where tokens are stored is absent. The tokens are created without requiring central storage of original card data.
It uses irreversible cryptographic techniques to generate tokens, hence, tokens cannot be reverse-mapped to original card data.
When to use:
- With high-security environments
- For cloud-native or modern payment architectures
- Businesses that prioritize maximum security over data recovery
How does tokenization work?
Here is a detailed step-by-step tokenization flow:
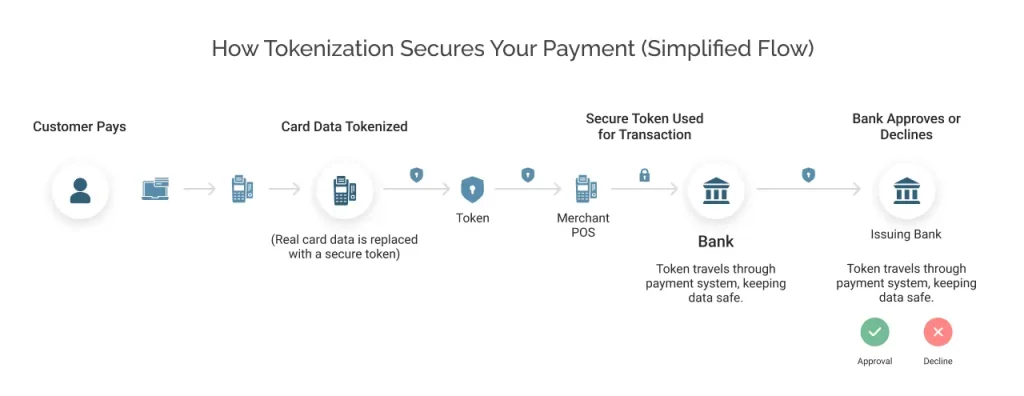
Step 1: Customer initiates payment process
The customer starts the payment process by inputting the card details at checkout.
Step 2: The Payment gateway or tokenization server receives the details
Once the payment details are received, it generates a token immediately, which is further saved in the vault.
Then these tokens are passed forward.
Step 3: Token returned to the merchant’s Point Of Sale (POS)
After successful generation and secured savings, the tokens returned to the merchant’s system. The merchant receives the following information:
- The unique token (e.g., tok_4f8q2n9x7r3m)
- Potentially non-sensitive metadata like last 4 digits of the card (for customer reference: ****1234)
- Card brand information (Visa, Mastercard, etc.)
- Non-sensitive expiration date or equivalent
Step 4: The Token is forwarded to the payment processor or the acquiring bank
From the merchant’s POS, the tokens are forwarded to the processor. Then the tokens are validated by the processor and forwarded to the acquiring bank.
Step 5: Card Network processes the transaction and de-tokenizes
The acquiring bank sends the tokenized transactions to the card network.
- The card network receives the token.
- It de-tokenizes the transaction by looking up the token in its vault and retrieving the original card data.
- It validates the token and original card details for consistency.
- It routes the transaction with the actual card data to the issuing bank (the bank that issued the customer’s card).
De-tokenization occurs here because card networks need access to the actual card data to route transactions correctly and manage fraud.
Step 6: Issuing Bank verifies and authorizes
The issuing bank receives the transaction details with the original card data and authorizes it. How?
- It checks if the account exists and is active
- It verifies sufficient funds or available credits
- It evaluates whether the transaction pattern is suspicious
- It may request additional verification, especially for high-risk transactions
Based on all this, the issuing bank sends back an approval or decline message.
Step 7: Response is sent back to the merchant
The approval or the decline message is sent backward through the payment flow:
Issuing Bank → Card Network → Acquiring Bank → Payment Processor → Merchant’s POS/Website.
If the response results in approval, then the transaction is completed.
Benefits of tokenization to businesses and their customers
Here are the key benefits that tokenization provides to businesses:
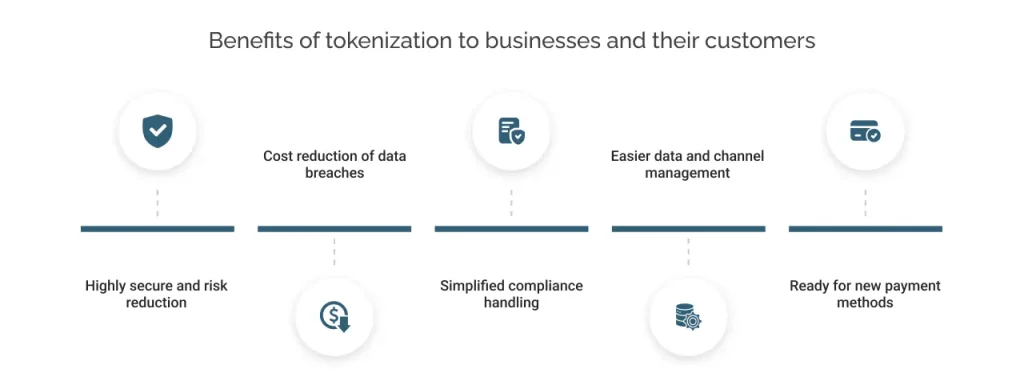
#1. Highly secure and risk reduction
Tokenization ensures that the real sensitive payment data is replaced with tokens, hence, even if hackers get access to this information, they cannot use it to cause any harm.
#2. Cost reduction of data breaches
Tokenization reduces the chances of data breaches significantly, which also cuts the cost of data breaches and protects brand reputation, gaining customer trust.
#3. Simplified compliance handling
As the actual card data is not stored, this maintains the PCI DSS scope. Therefore, audits and security requirements become simpler and cheaper.
#4. Easier data and channel management
The same token can work across online stores, mobile apps, and even in-store systems, so payment data remains consistent everywhere. This unified view makes it easier to manage customers, refunds, and loyalty programs across different channels.
#5. Ready for new payment methods
Tokenization works across multiple payment methods. So, you can safely add newer payment options without heavy customization. As you expand, tokenization scales with you and keeps payments secure.
Which types of businesses use tokenization for payments?
Any business that accepts payments from digital wallets and cards can use tokenization.
1. Online and subscription businesses
Many e-commerce stores use tokenization to protect saved cards, enable one-click checkout, and reduce fraud on online orders. While also, businesses offering subscription services such as SaaS, OTT, gyms, etc., use tokens to safely keep card data for automatic monthly or yearly billing.
2. Retail, restaurants, and travel
Businesses dealing in retail use tokenization with POS systems and mobile wallets such as Apple Pay, Google Pay, and more to secure in-store and contactless payments.
Restaurants, hotels, and travel agencies use it to store cards for reservations, no-show fees, deposits, and express checkout without exposing raw card data.
3. Marketplaces and B2B companies
Marketplaces and platforms like multi-seller sites, super apps, and more, use tokenization to safely process payments for many sellers while keeping buyer card data protected.
B2B companies use it for secure recurring invoices and contract billing. This reduces manual handling of client card details.
4. Banks, fintechs, and payment providers
Banks, fintechs, and payment processors rely on tokenization to secure transactions, reduce fraud, and support digital wallets and new payment experiences. Almost any business that takes credit or debit cards, whether online or offline, can benefit from using tokenization to make payments safer and smoother.
5. Businesses using Salesforce
Businesses leveraging Salesforce across various industries can benefit from tokenization. By securely storing and encrypting customers’ payment information, your Salesforce instance is well-protected.
To achieve this level of security, it is advised to leverage a Salesforce payment processor like ChargeOn. Designed natively for businesses using Salesforce, ChargeOn offers an effective tokenization solution.













